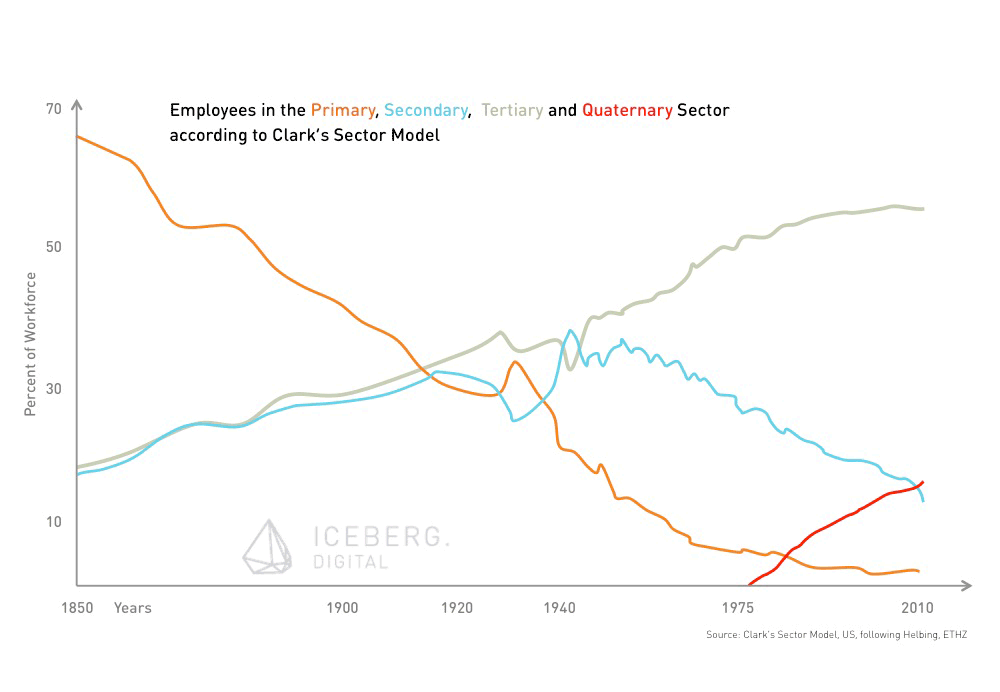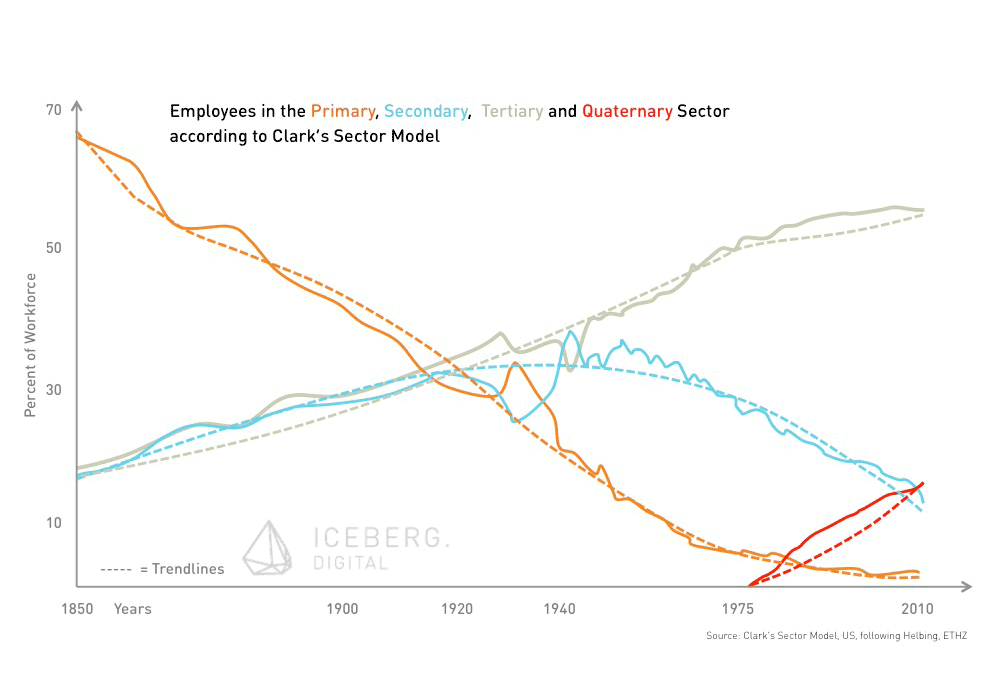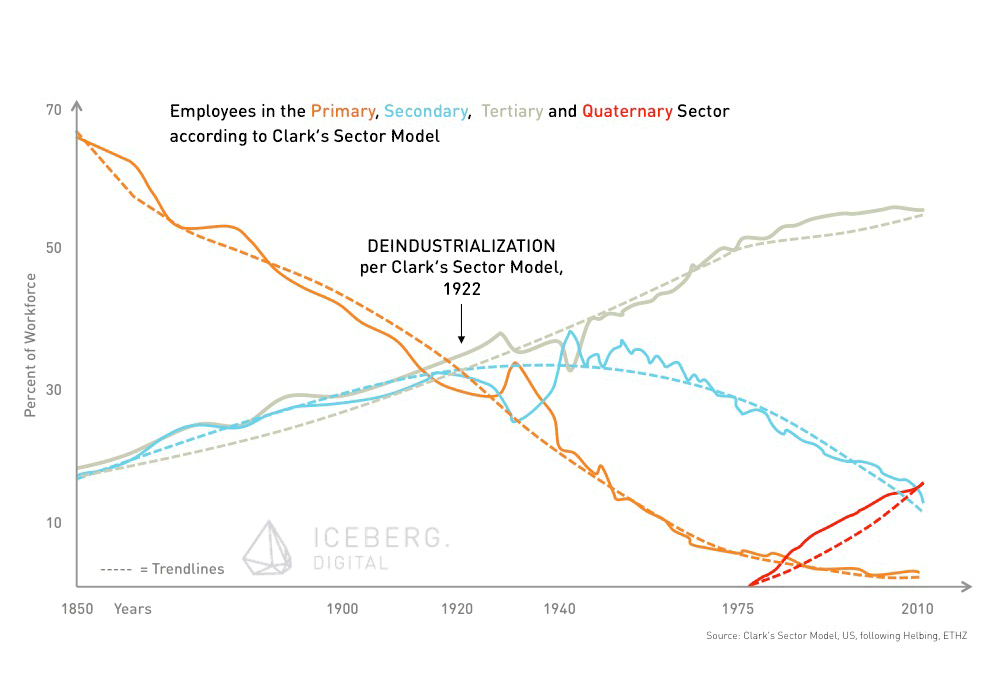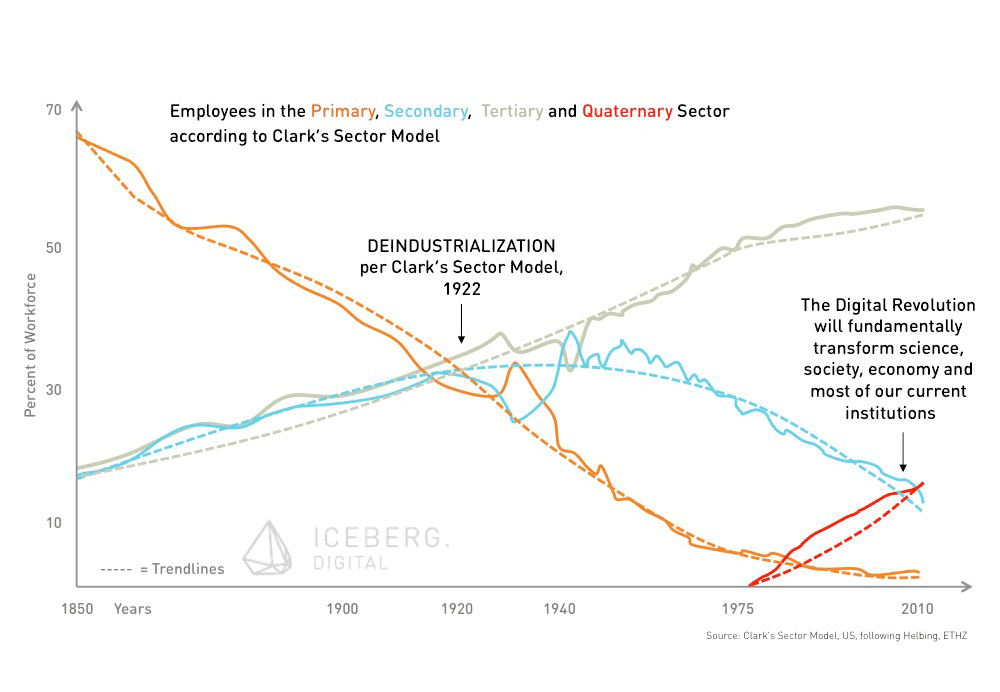
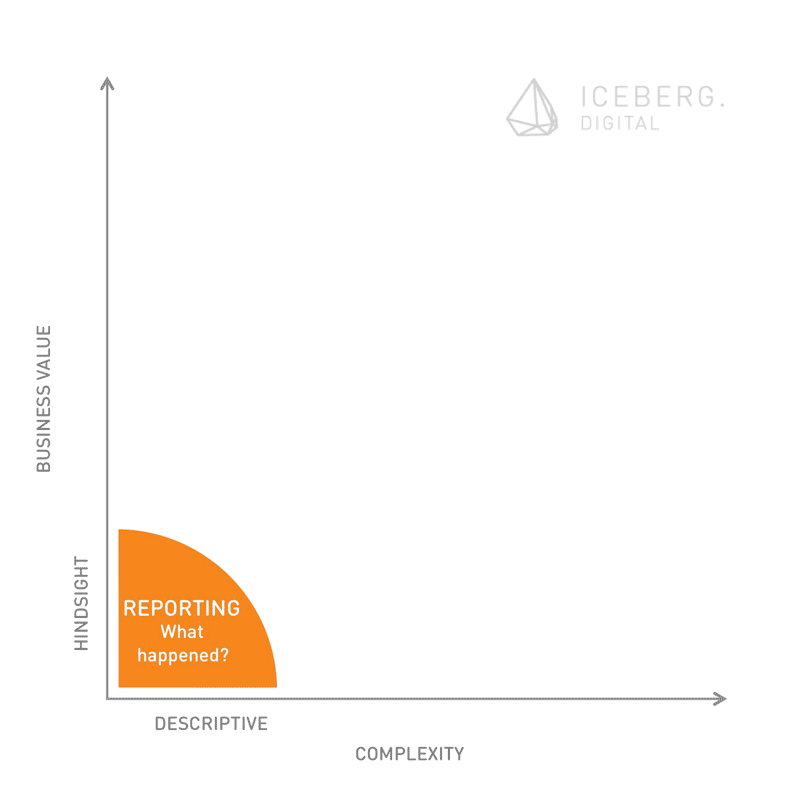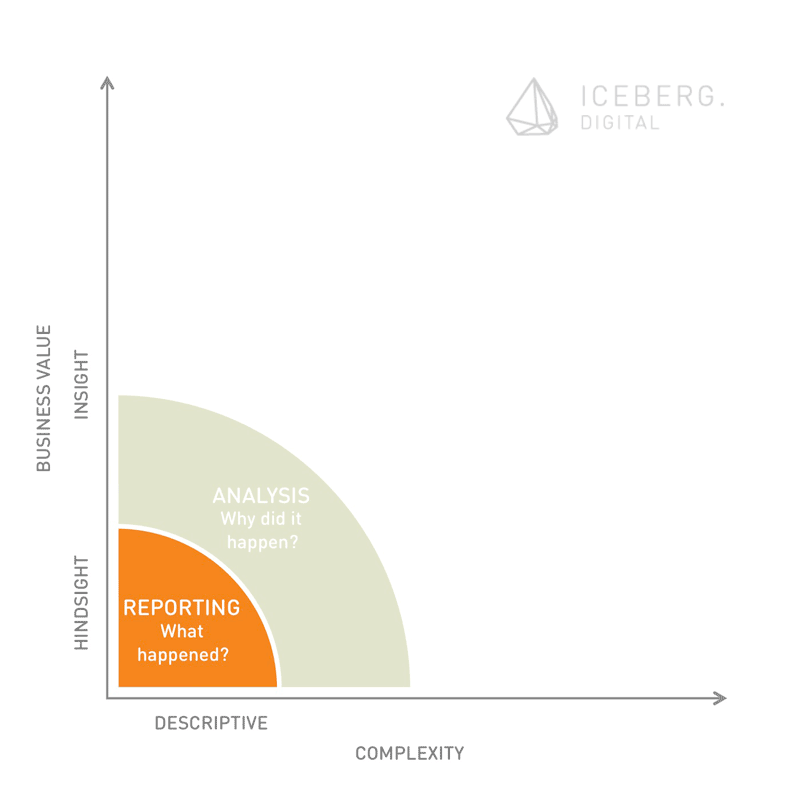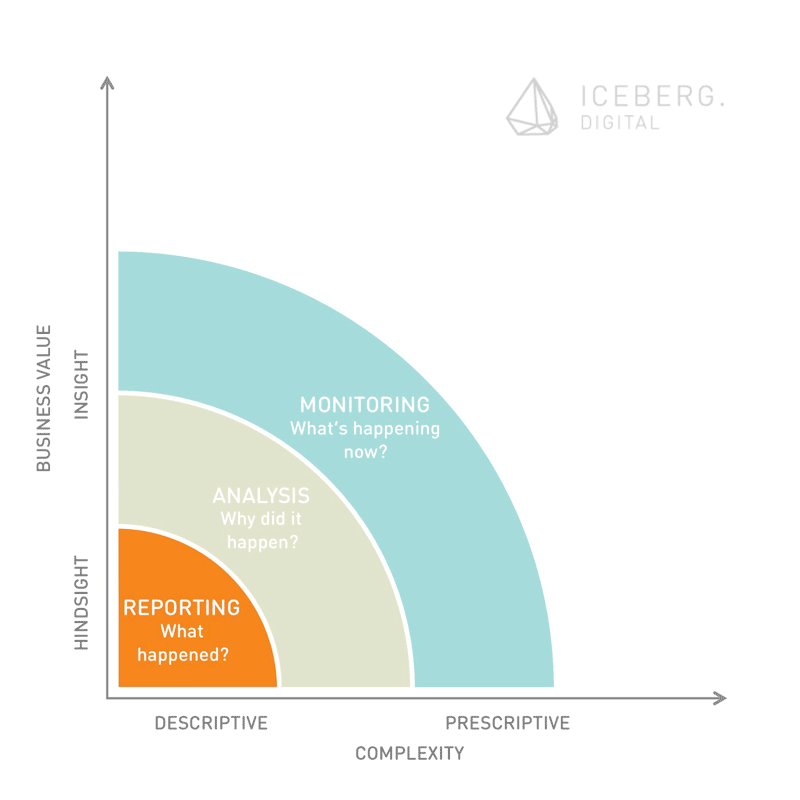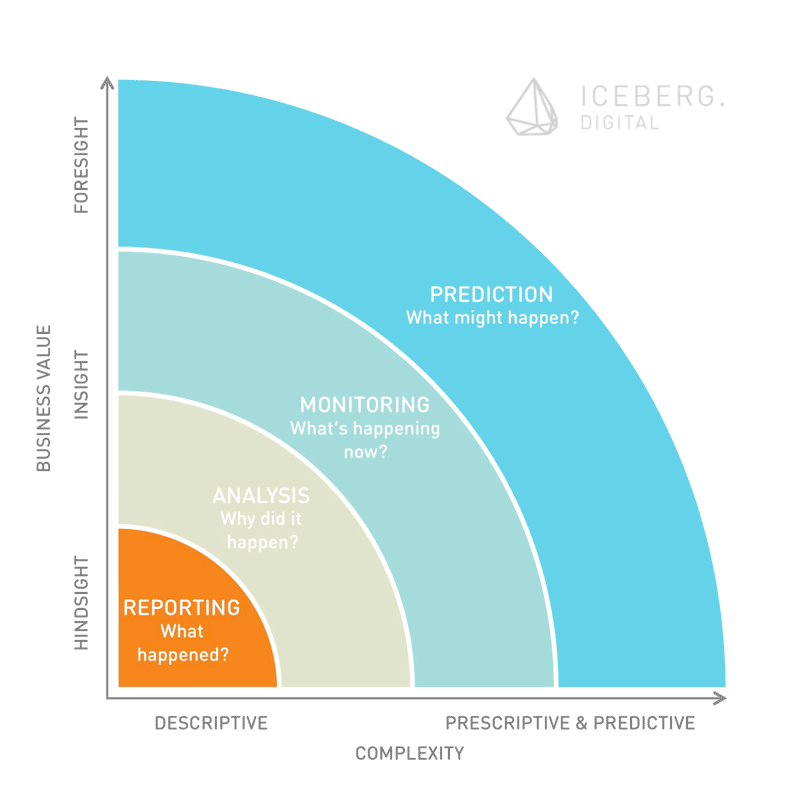
The digital economy is empowered and in turn causes an explosive growth of data. Bit it’s not the incomprehensible amount of data available that will impact our society. The real impetus is the potential insights companies, individuals or governments derive from this new, vast, and growing natural resource.
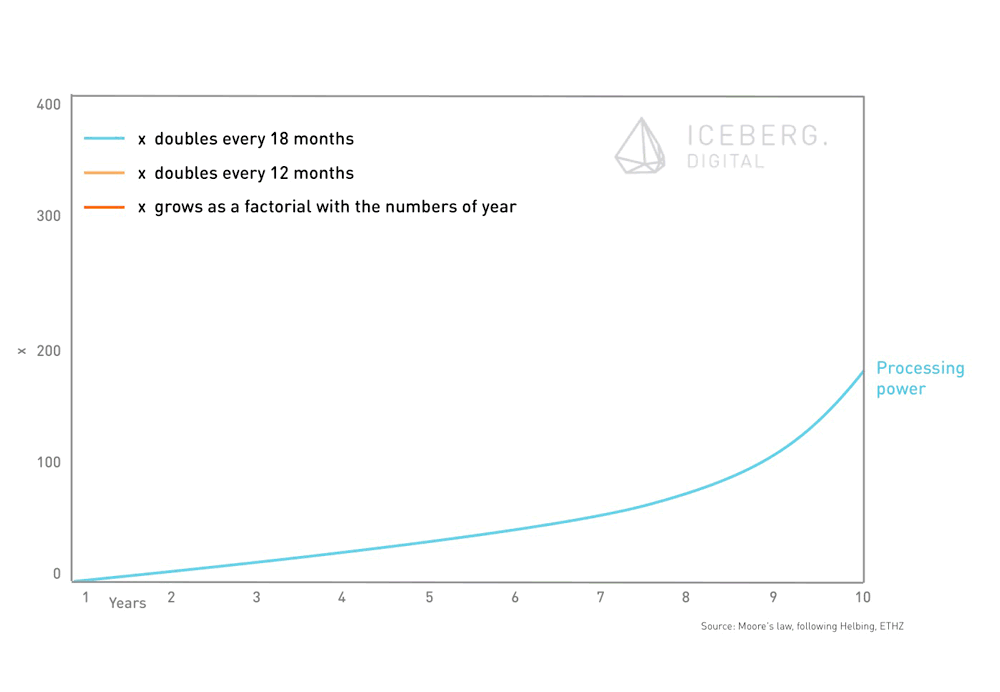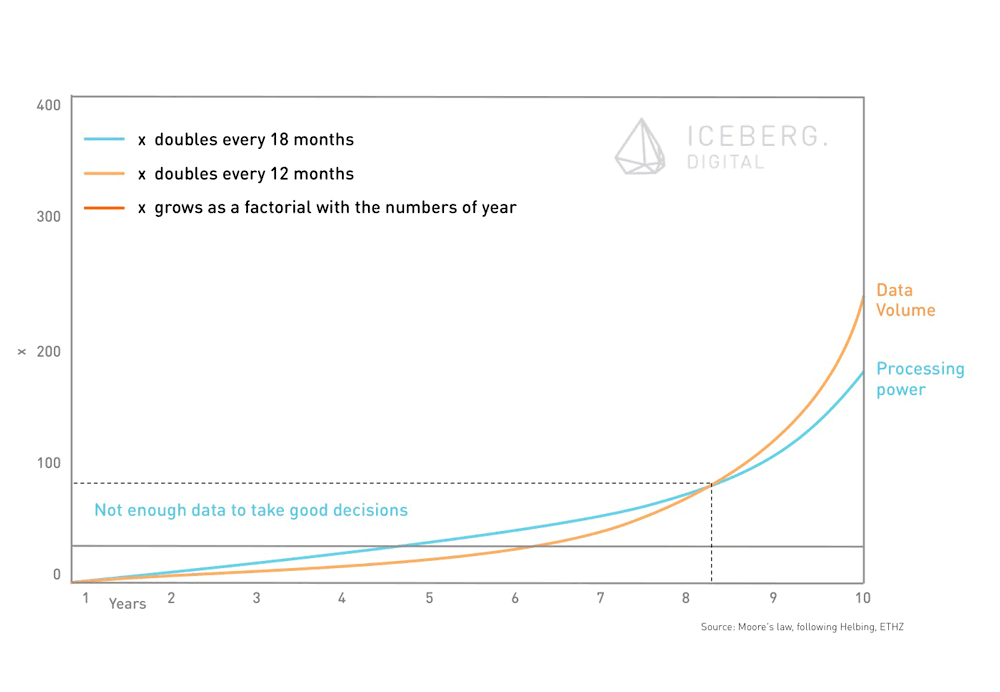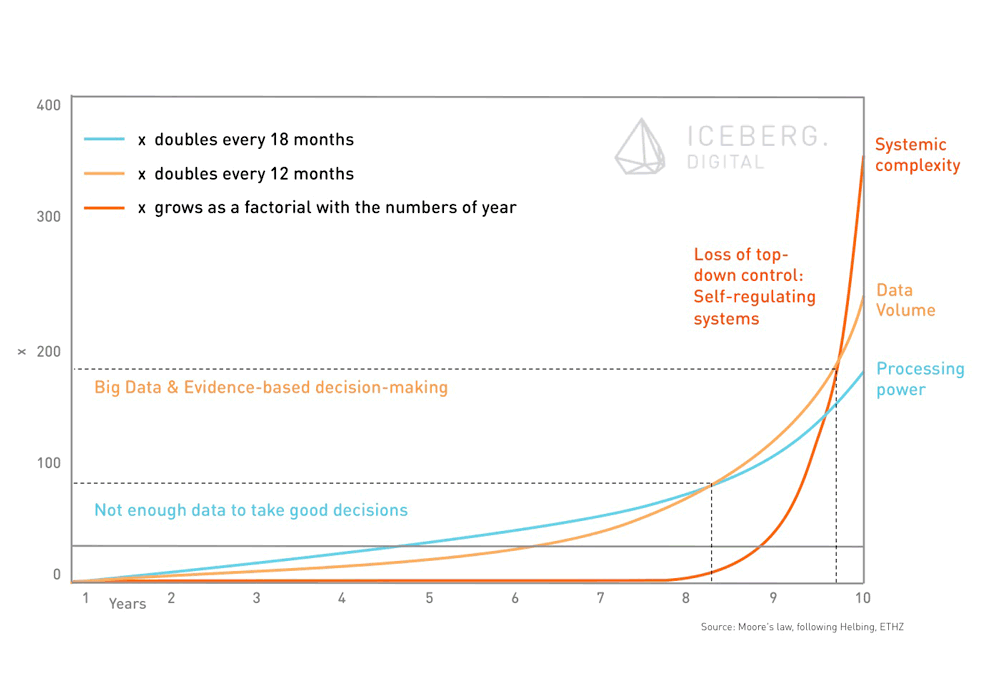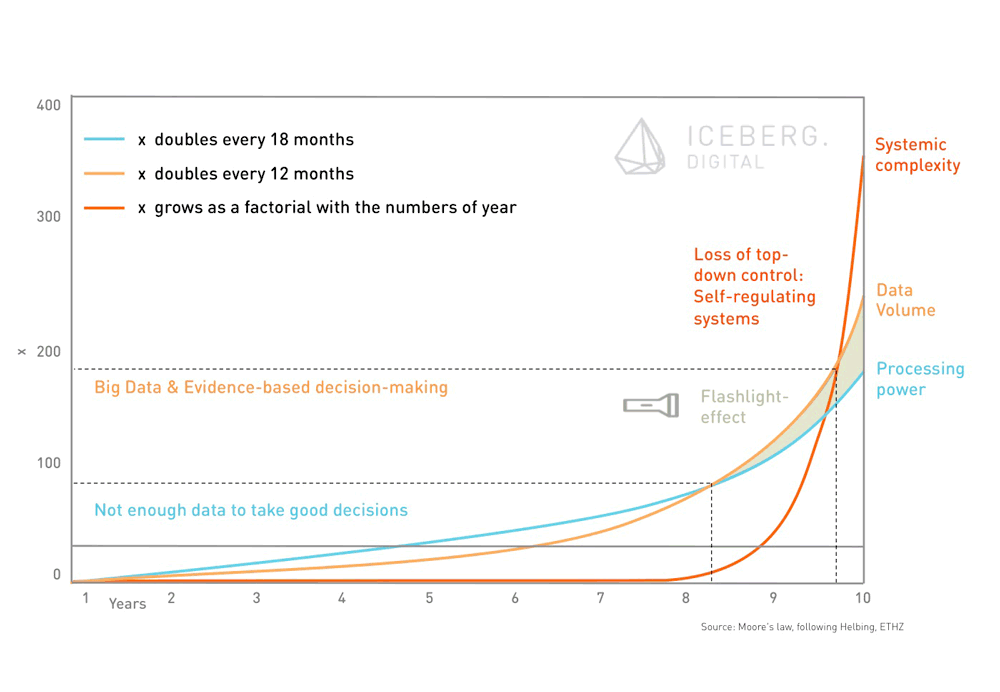
As shown in the below figure, interesting moments arise when different growth lines intersect. According to Moore’s law – which is still valid in 2015 – processing power doubles every 18 months. This is not only the reason why companies tend to present a new, fancy and more powerful laptop right after you bought yours. It allows to actually looking into data. The amount of available data grows at a faster pace than processing power. In the past, there was not enough data available to effectively evaluate this information and to take good decisions. Today’s processing power combined with new data storage and distributed paradigms (such as Hadoop) allow for evidence-based decision making.
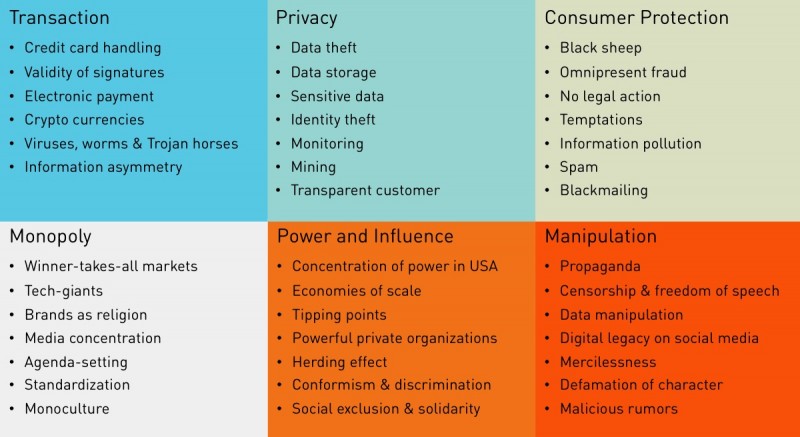
The other side of the coin is that we now have to decide what data is worth analyzing and last but not least which questions shall be asked. This restriction can be described as a flashlight effect. Companies or the government will only be able to see in the direction their analytics engines are pointed to.
Furthermore, increasing processing power and growth of data will lead to an even steeper curve of growing system complexity. Increasing system complexity requires more decentralized control mechanisms (Helbing, 2015). Today’s digital economy shows characteristics of monopoly markets. Google and Facebook lead primarily through top-down control. Maybe the change of governance structure at Google with the creation of the Alphabet holding organization is a first move in the inevitable direction towards decentralized and eventually self-regulating systems.