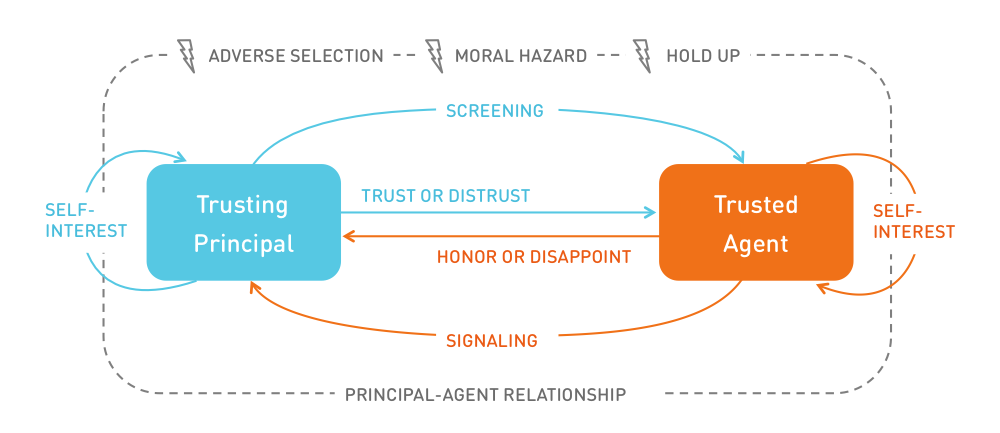
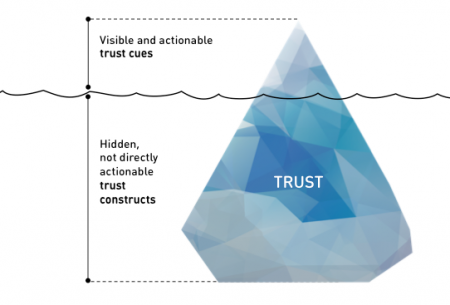
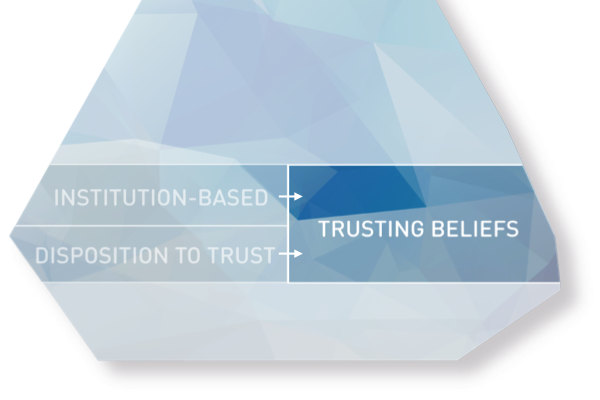
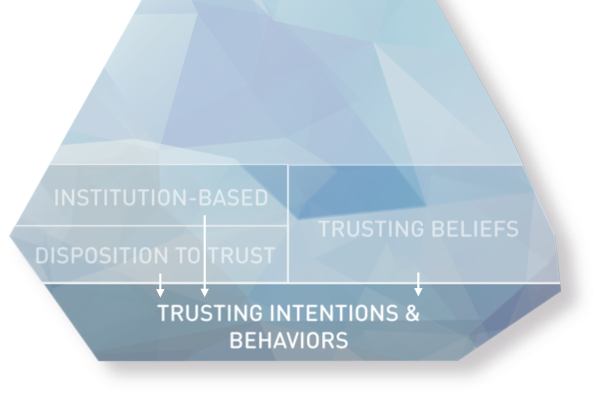
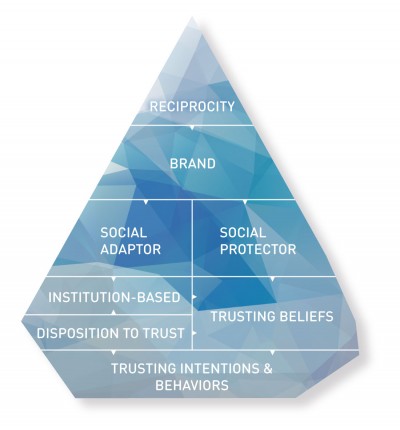
The quality of a brand’s digital presences (web, mobile, etc.) can foster brand reputation and enhance brand recognition. High site quality signals that the company has the required level of competence.
Important elements of design quality are usability, accessibility and the resulting user experience.
A particularly important paradigm leading the design process is processes “Privacy by Design”:
Privacy by Design advances the view that the future of privacy cannot be assured solely by compliance with legislation and regulatory frameworks; rather, privacy assurance must become an organization’s default mode (privacy by default) of operation. It is an approach to systems engineering, which takes privacy into account throughout the whole engineering process.
Privacy needs to be embedded, by default, during the architecture, design and construction of the processes. The demonstrated ability to secure and protect digital data needs to be part of the brand identity.
Done right, this design principle increases the perception of security. This refers to the perception that networks, computers, programs and in particular data is at all times protected from attack, damage or unauthorized access.