Chapter 1: Learn how pervasive consumer concerns about data privacy, unethical ad-driven business models, and the imbalance of power in digital interactions highlight the need for trust-building through transparency and regulation.
Chapter 8: Learn how AI’s rapid advancement and widespread adoption present both opportunities and challenges, requiring trust and ethical implementation for responsible deployment. Key concerns include privacy, accountability, transparency, bias, and regulatory adaptation, emphasizing the need for robust governance frameworks, explainable AI, and stakeholder trust to ensure AI’s positive societal impact.
Content in this chapter
- Market Failures in Centralized Identity Systems
- Technological Solutions: Web3 and Self-Sovereign Identity Systems
- Proof of Personhood: Ensuring Unique Digital Identity
- Economic Value Creation and Market Opportunities
- Future Directions and Research Imperatives
- Conclusion
- Digital Identity Landscape Explorer

Digital trust serves as the fundamental currency of the modern economy, yet its current architecture rests on increasingly unstable foundations. The internet’s original design omitted a native identity layer, creating what Kim Cameron, Microsoft’s Chief Architect of Identity, identified as the root cause of contemporary digital security and trust challenges (Cameron, 2005). This architectural gap has enabled the emergence of centralized identity monopolies that extract enormous value while imposing systemic risks on the global economy.
This article examines the economic and technological imperatives driving the transition from centralized to decentralized digital identity systems. As the digital economy continues to grow, now accounting for over 15 percent of global GDP, the costs associated with cybercrime, identity fraud, and AI-generated misinformation are rising in parallel, placing the foundations of digital trust at risk. Current centralized identity architectures generate systemic market failures, including information asymmetries, elevated transaction costs, privacy externalities, and concentrated market power. Based on interdisciplinary research spanning economics, technology, and public policy, the analysis evaluates emerging decentralized alternatives, including self-sovereign identity, proof-of-personhood protocols, and relationship-based verification systems, as exemplified by the First Person Project. These models offer mechanisms for restoring user agency, mitigating systemic vulnerabilities, and fostering inclusive economic participation. The discussion addresses challenges related to adoption dynamics, regulatory tensions, network effects, and implementation complexity, rather than resulting from sudden disruption. Digital identity innovation is expected to emerge through the gradual alignment of trust, technological capabilities, and institutional readiness. Ultimately, decentralized identity is presented not as a marginal technical refinement but as a socio-economic necessity for sustaining authentic human agency within AI-mediated digital ecosystems.
Cite article as (APA): Glinz, D. (2025). Decentralized Identity and the Economics of Digital Trust – Reclaiming Data Control in the AI Era (1.0). Zenodo. https://doi.org/10.5281/zenodo.15862391
The economic stakes are substantial and growing more urgent. The digital economy now accounts for over 15% of global GDP, while cybercrime and fraud impose significant costs, reaching $6 trillion globally in 2021 and projected to escalate to $10.5 trillion by 2025 (Hayat, 2022). The World Economic Forum estimates that even a modest 5% increase in a country’s digital trust level correlates with a $3,000 increase in GDP per capita, highlighting the direct relationship between identity infrastructure and economic prosperity (Hayat, 2022).
The challenge has intensified dramatically with advances in artificial intelligence. As AI becomes increasingly indistinguishable from human behavior online, the ability to distinguish between real people and bots presents critical threats to digital democracy and authentic human discourse (Adler et al., 2025). Recent research reveals that large language models, such as GPT-4, have convinced 54% of human evaluators that they are interacting with a real person, while deepfake fraud has increased tenfold globally between 2022 and 2023 (Zholudev et al., 2023; Jones & Bergen, 2024). This creates what economists might term a “trust premium,” where verified human interaction becomes increasingly valuable as synthetic alternatives proliferate.
This article argues that recapturing control over personal data and identity through decentralized technologies represents both an economic opportunity and an existential necessity in an AI-dominated landscape. We examine how market failures in current identity systems create deadweight losses (losses of economic efficiency when the optimal outcome is not achieved due to market distortions or interventions), analyze emerging solutions including self-sovereign identity (SSI) and proof-of-personhood (PoP) protocols, and assess the economic implications of transitioning to user-controlled identity architectures.
Market Failures in Centralized Identity Systems
Information Asymmetries and Transaction Costs
Current digital identity systems exhibit classic symptoms of market failure, primarily through information asymmetries and elevated transaction costs. In their seminal work on identity economics, Akerlof and Kranton (2000) demonstrate that identity choices are fundamental economic decisions influencing work effort, consumption, and saving behavior. In centralized systems, however, individuals lack meaningful control over their identity data, creating severe information asymmetries between service providers and users.
These asymmetries manifest in several ways. First, users cannot effectively monitor how their data is collected, processed, and monetized, leading to what economists term “surveillance capitalism,” where personal information generates value exclusively for platform owners (Zuboff, 2019). Second, the fragmentation of identity across multiple platforms creates search costs and switching costs that lock users into proprietary ecosystems, reducing market competition and innovation.
Transaction cost economics reveals additional inefficiencies. Cuypers et al. (2021) identify how high coordination costs in centralized systems prevent optimal resource allocation. Each new service requiring identity verification must independently establish trust relationships with users, duplicating verification processes and creating friction that inhibits digital commerce. Research by Granic et al. (2021) demonstrates that these transaction costs particularly burden small businesses and developing economies, creating barriers to digital participation.
Concentration and Market Power
Centralized identity systems exhibit extreme market concentration, with a handful of technology giants controlling a vast portion of the global digital identity infrastructure. This concentration creates several economic distortions. Platform economics research shows that identity providers can exploit network effects to maintain market dominance while extracting monopoly rents from both users and complementary service providers (Belleflamme & Peitz, 2018).
The monopolistic structure enables what economists call “platform envelopment,” where dominant identity providers expand into adjacent markets by leveraging their identity infrastructure as a competitive advantage. “Through envelopment, a provider in one platform market can enter another platform market, combining its functionality with that of the target in a multi‑platform bundle that leverages shared user relationships. Envelopers capture share by foreclosing an incumbent’s access to users […]” (Eisenmann, Parker, & Van Alstyne, 2011, p. 1270). This mechanism inhibits innovation and creates barriers to entry for potential competitors, resulting in reduced consumer welfare and slower technological progress.
Moreover, concentration creates systemic risk. The interdependence of digital services on centralized identity providers means that outages, security breaches, or policy changes at major platforms can have a cascading effect throughout the economy. The 2017 cyberattack on Estonia’s centralized infrastructure exemplifies how vulnerable centralized systems can destabilize entire national economies (Shumakova, 2020).
Privacy Externalities and Rights Deficits
Economic analysis reveals that centralized identity systems generate negative externalities through privacy violations, imposing costs on society while benefiting platform owners. The contemporary digital economy is predominantly driven by advertising-based revenue models, creating what Srnicek (2017) characterizes as platform capitalism that systematically collects and analyzes user-generated data to create comprehensive digital identity profiles.
This extraction follows a recursive pattern: advanced algorithms enable sophisticated digital products and services, which generate increased user engagement and more detailed behavioral data, creating an expanding data repository that drives corporate profitability (Alaimo & Kallinikos, 2017). However, users lack meaningful control over their personal data, creating what Fairfield terms “digital serfdom” (2017), a condition in which individuals become digital serfs – those who are dependent on corporate platforms for basic digital participation. The fundamental asymmetry lies in the fact that while users contribute valuable personal data, they lack meaningful control over how this information is collected, processed, and monetized (Nguyen et al., 2013). This data can be monetized without explicit consent or remuneration to the owner, creating increasingly “toxic” conditions for companies dealing with personal data. The amount of data grows at an astonishing rate, with users leaving traces of their digital activities, while the cost to acquire, manage, analyze, and protect vast volumes of user data increases, despite declining storage costs.
Central data stores become “honeypots” for hackers, and digital identities bear correlation risks when users employ identifiers across multiple platforms, enabling collusion to amass significant data about individuals without consent. The responsibility and complexity of managing personal data cannot be effectively outsourced to users, who typically prefer convenience over security. In contrast, low data quality and veracity lead to wrong decisions and damaged trust. The European Union’s General Data Protection Regulation (GDPR) represents an attempt to address these market failures through regulatory intervention, demanding that control over personal data be returned to individuals. However, compliance costs and complexity often favor large incumbents over smaller competitors, potentially reinforcing market concentration rather than promoting competition (Finck, 2019).

Technological Solutions: Web3 and Self-Sovereign Identity Systems
Privacy Externalities and Rights Deficits
T he emergence of Web3 fundamentally transforms personal information management and digital identity by shifting control from centralized corporate entities to individual users (Zheng et al., 2018). Traditional Web 2.0 infrastructure relies heavily on centralized authentication systems provided by major technology companies, such as Google or Facebook. While offering convenience, this model places control of digital identities and associated data in corporate hands, creating the power imbalances described earlier.
Web3 presents a paradigm shift in this architectural approach (Wang & De Filippi, 2020; Bassi & Bandirali, 2023). The Web3 framework introduces self-sovereign identity, analogous to a user-controlled digital passport that leverages blockchain technology to verify identity without disclosing unnecessary personal data (Preukschat & Reed, 2021). The technology facilitates selective attribute verification (e.g., age verification without birth date disclosure).
This transformation extends to data storage and sharing mechanisms. Web3 replaces centralized server storage with distributed systems, effectively creating individual digital vaults under user control. This architecture enables granular control over information sharing, including specific data elements, recipient selection, and duration of access. The system maintains transparent records of all transactions while preserving revocation capabilities, addressing the “toxicity” of personal data management that burdens centralized systems.
First Person Identity and Relationship-Based Verification
The concept of “First Person” identity refers to the identity that an individual experiences, owns, and has control over. The “I” in “I am.” This shift is foundational for building trusted interactions in decentralized, AI-driven ecosystems where control, verifiability, and privacy must originate with the person themselves. Unlike third-person identity (“The government says I am Daniel”) or second-person identity (“You are who I recognize you to be”), First Person Identity enables individuals to assert, “I am Daniel and can prove it with cryptographic credentials I control.”
The First Person Project, officially introduced at Geneva’s Global Digital Collaboration conference (GC 2025), represents a groundbreaking approach to solving the proof-of-personhood challenge through Verifiable Relationship Credentials (VRCs). Unlike centralized biometric systems such as World (formerly Worldcoin), which rely on iris scanning and global databases, First Person Credentials are built on Decentralized Identifiers (DIDs) and VRCs that provide cryptographic proof of genuine personal trust relationships. The idea of such a social is gaining traction in light of current challenges within the digital ecosystem. However, it builds on concepts that were articulated several years ago. As early as 2014, Doc Searls introduced the notion of First Person Technologies, stating: “We won’t get back our privacy, or make real progress toward real personal freedom, until we develop and deploy First Person Technologies for everybody. Without them, our democracies and marketplaces will also continue to be compromised, because both require those three virtues of privacy” (Searls, 2014). The economic implications of First Person Technologies are significant. Stewart Brand’s observation that “information wants to be free. Still, it also wants to be expensive” captures the fundamental tension at the heart of digital identity systems. Verified identity data possesses inherent value precisely because of its scarcity and authenticity in an environment increasingly saturated with synthetic content and automated interactions. This information asymmetry creates a “trust premium” where verified human interaction becomes increasingly valuable as synthetic alternatives proliferate.
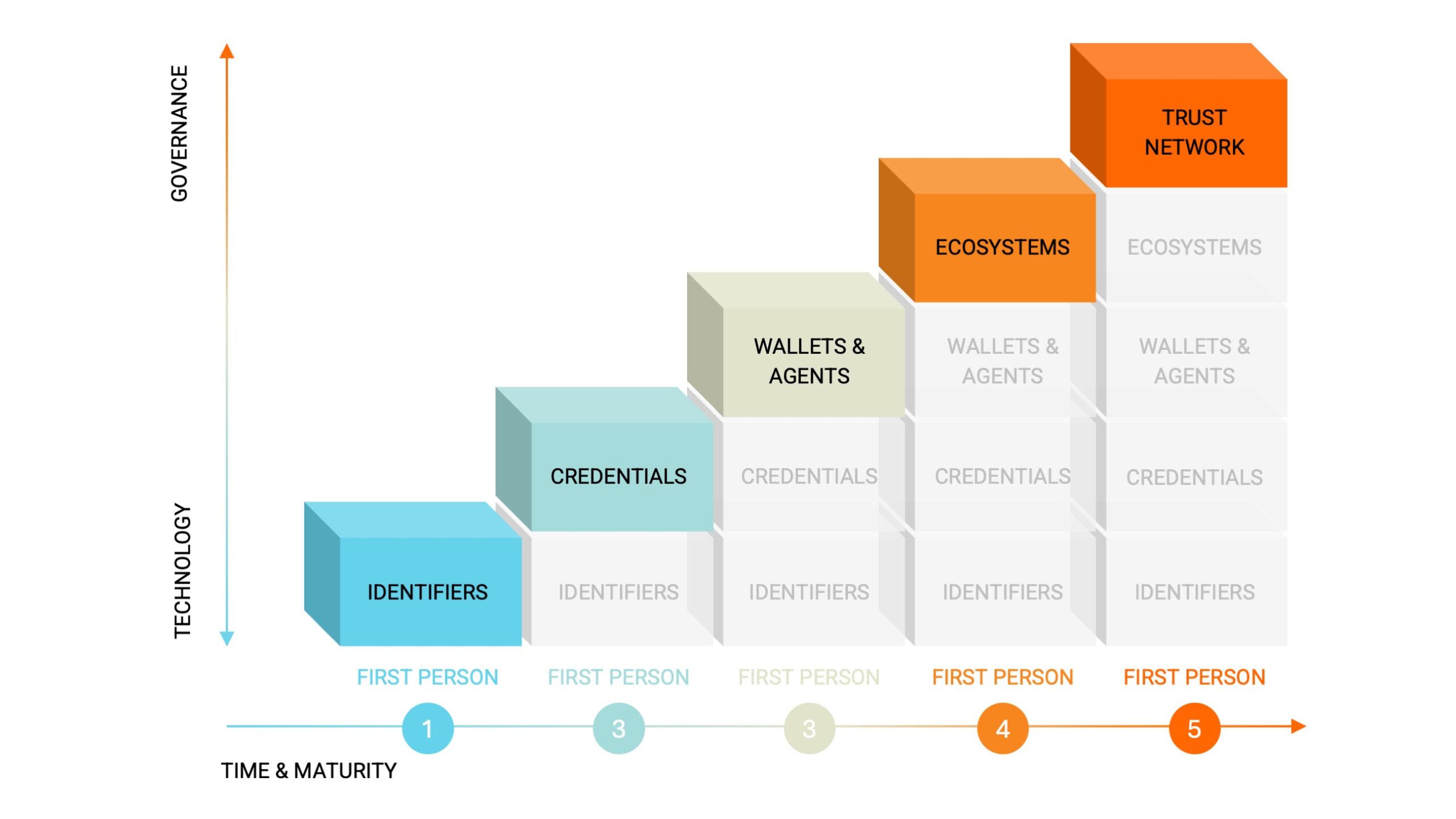
This approach leverages the natural human tendency to form verifiable social connections while utilizing advanced cryptographic techniques to ensure privacy and security. First person technologies should enable individuals to create a decentralized social graph that operates independently of any centralized authority, including corporations or governments. Such a system operates through sophisticated personal attestations where individuals vouch for their relationships with others, creating a decentralized network of trust that addresses both authenticity and uniqueness without surrendering personal data to centralized authorities. Hence, as digital ecosystems become increasingly opaque and centralized, the First Person Project introduces a transformative approach: a bottom-up, user-controlled framework for digital identity and trust (Reed & O’Donnell, 2025). This paradigm is operationalized through five interdependent domains that collectively form a decentralized architecture for verifiable, privacy-preserving human interactions. The following section presents the foundational components of identifiers, credentials, wallets, agents, ecosystems, and trust networks, out
lining their interrelations and practical relevance.
1 Identifiers: Establishing Self-Sovereign Anchors: At the core of the First Person architecture are Decentralized Identifiers (DIDs), which serve as unique, persistent references to a user’s digital identity. These authorities do not issue these identifiers; instead, they are cryptographically self-certifying. This design ensures that users retain complete control over how their identities are used and shared across digital environments.
Unlike early DID systems that were tethered to specific blockchains or domains, the First Person approach emphasizes portability and independence. Self-certifying identifiers are created using public-private key pairs and are not bound to any single technological infrastructure. As a result, users can relocate their identifiers freely. This principle aligns with the standardization work of the Linux Foundation’s Trust over IP (ToIP) project, which supports global interoperability and adoption.
2 Credentials – Verifying Personhood While Preserving Privacy: Identification alone does not suffice; the authenticity of identity must also be verified. Verifiable credentials (VCs), as defined by the World Wide Web Consortium (W3C), provide cryptographically secure attestations of identity attributes. Within the First Person Project, particular emphasis is placed on personhood credentials, which confirm that the holder is a unique and living human being, without revealing personally identifying information.
Two primary requirements govern the issuance of personhood credentials. First, each credential must be issued only once per person to prevent replication or misuse. Second, the system must support unlinkable pseudonymity, allowing individuals to present zero-knowledge proofs without disclosing unnecessary information or linking separate interactions.
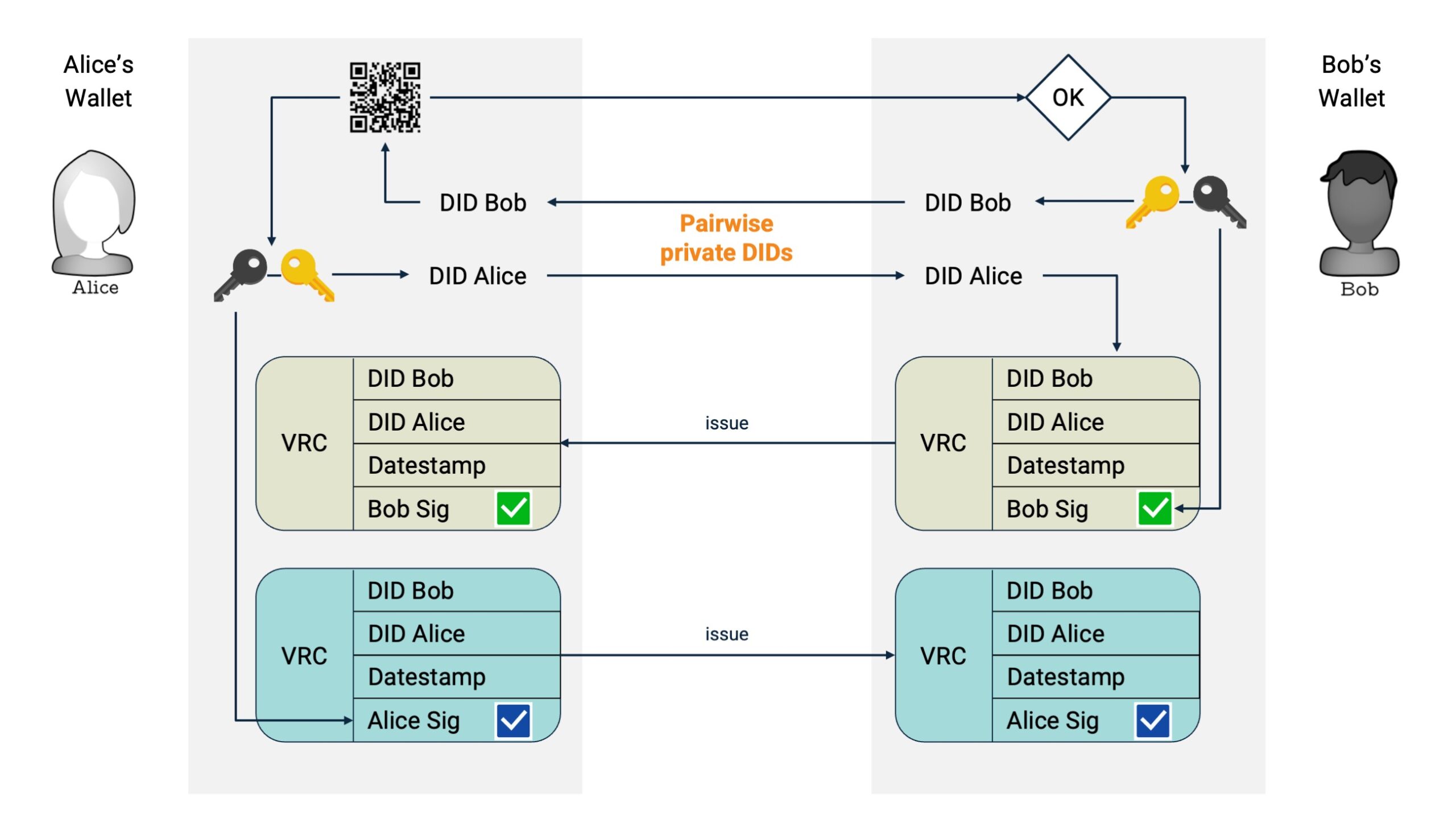
A key innovation in this domain is the use of Verifiable Relationship Credentials (VRCs). These credentials are generated through decentralized, peer-to-peer interactions and serve as cryptographic proof of genuine human relationships. This approach replaces, for example, CAPTCHA-like mechanisms and biometric identifiers with trust rooted in personal connections, verified in a privacy-preserving manner.
3 Wallets and Agents- Interfaces for Digital Autonomy: To manage identifiers and credentials effectively, users need interfaces that provide both functionality and control. In the First Person architecture, these interfaces consist of wallets and software agents. Wallets store cryptographic materials, while agents carry out trust-related tasks such as authentication, data exchange, and credential issuance.
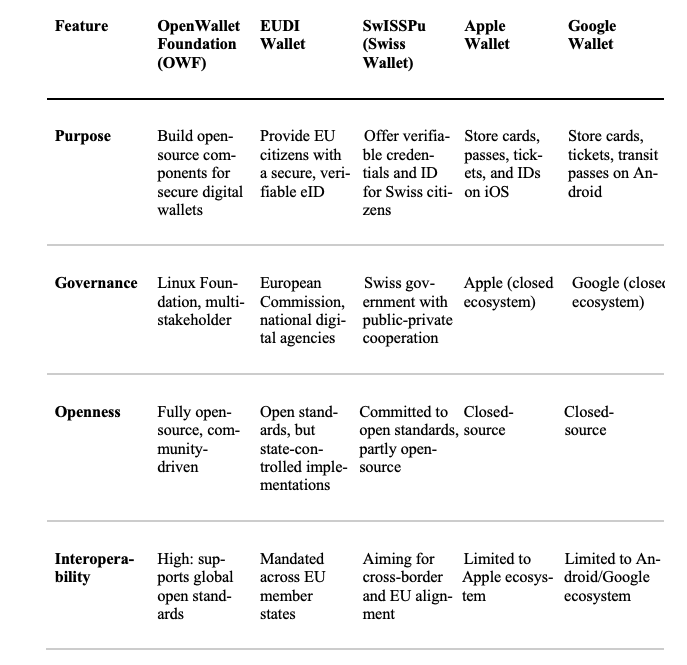
Software agents are more than passive tools. They actively perform predefined trust tasks, allowing individuals to manage interactions without relying on centralized intermediaries. Open-source projects, such as the Open Wallet Foundation (OWF, https://openwallet.foundation) and the Solid Pods Initiative (https://solidproject.org), provide the technical foundation for these tools. Increasingly, the term “agentic wallet” is used to describe systems that combine secure storage with user-centric functionality. Wallets associated with OWF are fundamentally characterized by their modular, open-source, and non-prescriptive architecture. The OWF does not produce a single wallet product; instead, it provides a shared, open-source codebase and reference components that enable governments, private entities, or developers to build interoperable, privacy-preserving, and user-centric digital wallets. The focus is on allowing a plurality of implementations, aligned with open standards such as Decentralized Identifiers (DIDs), Verifiable Credentials (VCs), and zero-knowledge proofs (ZKPs). In contrast, other digital wallets discussed in the comparative analysis, namely the EUDI Wallet, SwISSPu, Apple Wallet, and Google Wallet, are more centralized, vertically integrated solutions with predefined governance, scope, and constraints, as illustrated in the table below.
Agents support use cases such as secure messaging, mutual authentication, and reputation building. For instance, individuals can issue “relationship cards” to one another, which contain contact information or attestations of skills and roles. All interactions are peer-to-peer and cryptographically secured, ensuring trust without surveillance.
4 Ecosystems – Contextual Frameworks for Trust: Digital identity does not exist in isolation. Trust must be contextualized within digital trust ecosystems, where shared rules, schemas, and governance structures define how credentials are used and verified.
These ecosystems follow the well-established issuer–holder–verifier model. In this model, a trusted authority (the issuer) attests to an attribute of an individual (the holder), which can then be verified by a third party (the verifier). Governance bodies define the trust registries, credential schemas, and data exchange protocols necessary for operation.
The Linux Foundation has begun applying this model to its own open-source development workflows. Motivated by threats such as malware injection attacks, the Foundation aims to implement personhood credentials as a means of authenticating developers and securing critical infrastructure. This represents one of the first real-world deployments of the First Person architecture at scale.
5 Trust Networks – Enabling Interoperability Across Ecosystems: To realize the full potential of decentralized identity, credentials must be portable across multiple ecosystems. This requires the creation of interoperable trust networks that connect various digital trust systems and allow relationships and credentials to be reused across contexts.
An organization called Ayra (https://ayra.forum) has been established to address this need. Its mission is to build bridges between distinct ecosystems and support interoperable standards for trust exchange. The First Person Network operates as one of these interconnected systems, aligning with Ayra’s broader goal of a federated, user-controlled identity infrastructure.
Global Policy Context and Regulatory Innovation
T he development of proof-of-personhood systems takes place within a complex global regulatory environment, where different jurisdictions are adopting varying approaches to digital identity. Switzerland’s e-ID initiative exemplifies this complexity. After voters rejected a 2021 proposal involving private companies over privacy concerns, the government pivoted to a self-sovereign identity model called SWIYU. This new approach emphasizes decentralized data storage, user control, and privacy-by-design principles, though it still faces challenges, including a referendum vote scheduled for September 2025.
The European Union’s Digital Identity Wallet framework adopts a distinct approach, prioritizing user control and interoperability while maintaining regulatory oversight under the eIDAS 2.0 regulation. Meanwhile, emerging markets are experimenting with entirely new models that may leapfrog traditional identity systems altogether, creating opportunities for inclusive economic development through verifiable digital credentials.
The First Person Project’s decentralized approach presents both opportunities and challenges within this regulatory landscape. Its emphasis on individual control and privacy aligns with growing concerns about surveillance capitalism and data exploitation. However, regulators may struggle with oversight and compliance in systems designed to operate without central authorities, creating tension between innovation and traditional governance frameworks.
Implementation Complexity and Critical Adoption Factors
The technical architecture of SSI systems is built on several key innovations: Decentralized Identifiers (DIDs) that enable user-controlled identity creation, Verifiable Credentials (VCs) that allow for the privacy-preserving presentation of attested information, and zero-knowledge proofs that enable selective disclosure without revealing unnecessary personal data. The W3C standardization of both DIDs and Verifiable Credentials provides the interoperability foundations necessary for network effects.
However, critics point out that “a web of trust can feel like a pile of disconnected threads”. Establishing coherent and verifiable relationships across different contexts remains a significant technical challenge. Any effective proof-of-personhood solution must satisfy several essential criteria (Windley, 2025): it must be tangible (grounded in real-world interactions that are difficult to fabricate), usable (with intuitive interface design that doesn’t burden users), useful (addressing genuine problems that people face), portable (functioning across various platforms and services), contextual (providing appropriate verification levels for different use cases), and actionable (enabling concrete decisions and protective measures).
The complexity of an identity layer can only be solved by drawing on multiple concepts and technologies. While a robust trust framework, in terms of binding commitments to governance rules, remains essential, blockchain mechanisms can be leveraged to access personal data stores and facilitate value transfers. There will not be a single, centrally owned solution or architecture, but rather a consortium of different, autonomous solution providers with their interoperable components.
The adoption of solutions like the First Person Project faces significant complexity that extends beyond technical implementation to encompass network effects, user behavior, and coordination challenges within the ecosystem. The success of relationship-based verification systems depends critically on achieving sufficient network density and trust relationships to provide meaningful proof-of-personhood verification. This creates a fundamental coordination problem: early adopters bear the costs of participation without immediate benefits, while the system only becomes valuable once a critical mass of users and verifiers participate.
User experience complexity represents another critical adoption barrier. While the First Person Project aims to leverage natural human relationship formation, translating these social connections into cryptographic proofs requires users to understand and manage complex technical processes. The system must strike a balance between the sophistication needed for security and the intuitive simplicity necessary for mass adoption. Research on technology adoption reveals that perceived ease of use and perceived usefulness are primary determinants of user acceptance, particularly for systems that require behavioral change (Stockburger et al., 2021).
Economic incentive alignment poses additional challenges for adoption. Unlike centralized systems, where platform owners can subsidize user acquisition, decentralized identity systems must create value propositions that cater to multiple stakeholder groups simultaneously. Credential issuers (governments, educational institutions, employers) must invest in new infrastructure and processes. Verifiers (service providers, platforms) must modify their authentication systems. Users must learn new identity management practices. The absence of a central coordinating entity to manage these transitions means that adoption requires organic coordination across multiple industries and use cases.
The urgency of the AI authenticity crisis amplifies the critical nature of this adoption challenge (Adler et al., 2025). As synthetic content generation capabilities advance rapidly, the window for establishing human verification systems may be limited. A delay in adoption could result in a scenario where distinguishing between human and AI-generated content becomes economically or technically infeasible, potentially undermining democratic discourse and economic trust permanently. This temporal pressure creates both an urgency for deployment and a risk of prematurely adopting systems that are not sufficiently tested.
Furthermore, the success of the First Person Project depends on maintaining the delicate balance between privacy preservation and verification effectiveness. The relationship-based approach must prove resilient against sophisticated attacks while remaining usable for ordinary users who lack technical expertise. The system’s cryptographic foundations must withstand both current threats and anticipated future challenges, including potential quantum computing attacks on current encryption methods.
The Gradual Emergence of Digital Identity: Evolution, Not Explosion
The question of when digital identity will reach mainstream adoption is increasingly pressing. Industry voices are converging around the idea that digital identity, particularly decentralized solutions and broader Empowerment Technologies, will not arrive in a single, disruptive wave. Instead, adoption will be gradual, driven by fragmented innovations that eventually converge into robust ecosystems. The user-controlled digital identity framework presented above (Figure 1) already accounts for this assumption.
In a recent article, Cooper (2025) outlines a pragmatic four-phase timeline for the emergence of digital identity:
- 2025: A fragmented landscape of identity tools, including single sign-on (SSO), biometrics, and early decentralized solutions.
- 2025–2026: The rise of digital wallets from major platforms and initial government-backed identity credentials.
- 2027–2028: Cross-platform identity portability, interoperable decentralized identifiers (DIDs), and AI-managed identity permissions.
- 2029–2030: Mature digital identity ecosystems, where identity infrastructure supports agent-to-agent negotiation and deeply integrated services.
This staged progression contrasts with Gartner’s (2018) more optimistic forecast, which predicted 500 million active digital identity wallets by 2026. Cooper’s assessment presents a more grounded view, emphasizing that the real-world adoption of digital identity depends on a confluence of technical, regulatory, and behavioral factors. Crucially, digital identity adoption will likely mirror the early internet, with innovation emerging in pockets of user value. These hotspots, whether driven by new interfaces, regulatory demands, or local market needs, will gradually produce strong network effects. As with the rise of social media platforms, it may not be the first or even fifth solution that succeeds, but the one that assembles existing capabilities in a novel way.
Breakthrough moments are expected to catalyze adoption. This could occur through a digital staff passport, AI-enabled payment flows, or decentralized Know Your Customer (KYC) systems emerging from countries such as Nigeria or Brazil, where large markets enable practical innovation to scale rapidly. As Smith notes, digital identity will evolve slowly, requiring significant design work and ecosystem coordination (2025). Key dependencies include user experience design, viable business models, standards development, and liability frameworks. Until these are aligned, adoption will remain patchy but promising. Rather than a sudden shift, the digital identity market is emerging through the steady convergence of technology, trust, and timing.”
Economic Rationale
P roof-of-personhood protocols address a fundamental challenge in digital systems: ensuring that each real human controls at most one identity within a given context. This uniqueness constraint prevents Sybil attacks where malicious actors create multiple false identities to manipulate systems or extract disproportionate value.
The economic importance of PoP extends beyond security to questions of fairness and resource distribution. Borge et al. (2017) demonstrate how PoP can enable “redemocratization” of digital systems by ensuring that governance rights, universal basic income distributions, or other benefits accrue to real individuals rather than being concentrated among those with technical resources to create multiple identities.
Technical Approaches and Trade-offs
Current PoP implementations employ various technical strategies, each with distinct economic implications. Biometric approaches, such as World’s iris scanning, promise high accuracy but raise concerns about privacy and surveillance that could generate negative externalities. The concentration of biometric data creates systemic risks and potential for authoritarian abuse.
Social verification methods, exemplified by the Proof of Humanity project, utilize human networks to verify the uniqueness of identities. These approaches preserve privacy better than biometric systems but face scalability challenges and vulnerability to coordinated attacks. The economic cost of maintaining social verification networks may limit their applicability to large-scale systems.
Cryptographic approaches, such as the First Person Project’s Verifiable Relationship Credentials, offer promising alternatives that strike a balance between privacy, security, and scalability. By using personal relationships as verification foundations, these systems can resist Sybil attacks while preserving anonymity and avoiding centralized biometric databases.
While World’s biometric approach has drawn criticism regarding surveillance risks and loss of digital anonymity, First Person Credentials preserve privacy through relationship-based verification, aligning with Vitalik Buterin’s advocacy for “pluralistic identity” systems (2023). Buterin’s critique of centralized biometric systems highlights fundamental concerns about power concentration, erosion of privacy, and the potential for authoritarian surveillance.
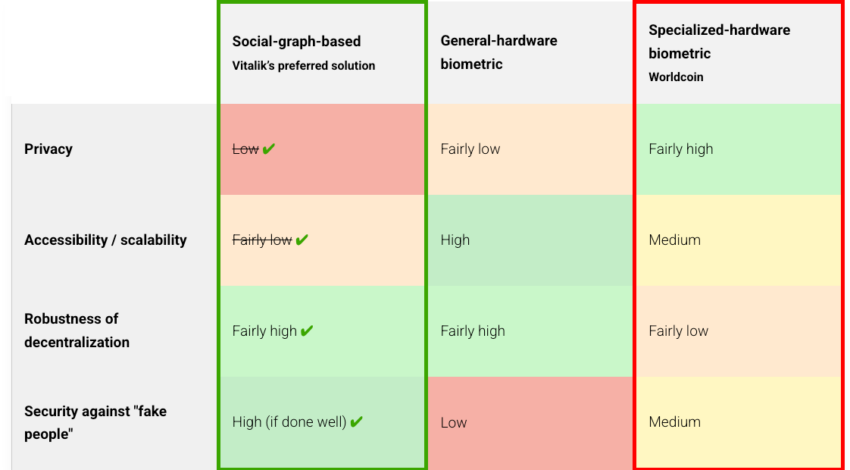
The fundamental distinction lies in data control architecture: centralized systems concentrate valuable identity information within single entities, creating attractive targets for surveillance, data breaches, and cyberattacks. These “honeypot” architectures also create single points of failure that can compromise millions of users simultaneously, exemplifying the systemic risks identified in Estonia’s 2017 cyberattack experience.
Decentralized trust networks distribute this value across communities, maintaining both security and democratic oversight while preserving the essential economic value of verified human participation. This distributed approach makes the system more resilient to attack, more resistant to censorship, and more aligned with democratic principles of distributed power. Other alternatives, such as government-issued digital IDs, knowledge-based authentication, and hardware security keys, each offer different trade-offs between security, privacy, usability, and scalability.
Blockchain Limitations and Multi-Technology Solutions
The potential of blockchain technology as a framework for personal data management warrants critical examination. While its decentralized architecture and cryptographic security mechanisms offer promising features for identity management (Dunphy & Petitcolas, 2018), a comprehensive analysis of its capabilities and limitations is essential. The technology’s inherent properties of immutability and distributed consensus present both opportunities and challenges for personal data handling (Yang et al., 2019).
Several critical limitations must be addressed: The distributed ledger is forged by consensus and lacks strong governance by design, meaning protocol changes through hard forks could dramatically impair identity schemes. Personal data stored directly on the ledger would quickly result in breaches of data protection regulations. Transferring information across blockchains can be difficult, potentially impairing portability and interoperability. Unique identifiers stored on the ledger would trigger immediate correlation risks, and identity information on blockchain cannot easily be revoked, which is critical for managing claims and entitlements.
Following this analysis, the complexity of an identity layer can only be solved by drawing on multiple concepts and technologies. While a robust trust framework in terms of binding commitments to governance rules remains essential, blockchain mechanisms can be leveraged specifically for accessing personal data stores and handling value transfers. The future will likely feature not a single, centrally owned solution but rather a consortium of different, autonomous solution providers with interoperable components.
Two-Sided Market Dynamics
Identity platforms exhibit classic two-sided market properties, where value creation depends on participation from multiple stakeholder groups. Credential issuers (governments, universities, employers) must participate to provide valuable attestations, while verifiers (service providers, employers, institutions) must accept credentials to create utility for holders.
Research on platform economics reveals that successful two-sided markets require careful attention to pricing and adoption strategies. Unlike traditional platforms, where one side often subsidizes the other, identity platforms must provide value to all participants simultaneously. This creates more complex coordination challenges but also opportunities for more equitable value distribution.
The presence of network effects means that successful identity platforms could achieve significant market power. However, the open standards underlying SSI and PoP systems may prevent winner-take-all outcomes by enabling interoperability between competing platforms. This technical architecture could preserve competitive dynamics while capturing network benefits.
Interoperability and Standards
The W3C’s standardization of DIDs and Verifiable Credentials lays the foundation for interoperability that could prevent platform fragmentation. Unlike proprietary identity systems that create switching costs and lock-in effects, standard-based SSI implementations enable users to switch between service providers without losing their identity data.
This interoperability has important economic implications. Competition between identity service providers could drive innovation and reduce prices while preserving network effects. Users gain negotiating power when they can easily switch providers, constraining the ability of any single platform to extract monopoly rents.
However, achieving true interoperability requires coordination on governance frameworks and technical standards beyond basic protocols. Research by the Decentralized Identity Foundation and other standards bodies continues to address these challenges; however, significant work remains to be done to achieve seamless, cross-platform identity experiences.
Regulatory Frameworks and Economic Policy
Privacy regulations, such as GDPR and CCPA, represent government interventions designed to address market failures in data markets. These regulations grant users rights over their personal data and impose obligations on data controllers, effectively redistributing power in digital markets.
However, regulatory compliance often favors large incumbents, who can more easily absorb compliance costs than smaller competitors. This dynamic may inadvertently reinforce market concentration rather than promoting competition. SSI systems offer an alternative approach by making privacy protection a technical property rather than a regulatory requirement.
National governments increasingly recognize digital identity infrastructure as critical for economic sovereignty. Control over identity systems affects a nation’s ability to regulate its digital economy, protect citizen privacy, and maintain independence from foreign technology providers.
The European Union’s eIDAS 2.0 framework and Digital Identity Wallet initiative exemplify efforts to create sovereign digital identity infrastructure. These initiatives aim to reduce dependence on U.S. technology giants while providing citizens with privacy-preserving identity tools that comply with European values and regulations.
Access to a digital identity represents a prerequisite for economic participation in modern societies. Research by Wang and De Filippi (2020) demonstrates how SSI systems can accelerate inclusive development by providing marginalized populations with verifiable digital identities, enabling access to financial services, education, and economic opportunities.
The cost-effectiveness of SSI implementations makes them particularly attractive for developing economies. Rather than building expensive centralized infrastructure, governments can leverage blockchain networks and open-source SSI implementations to provide citizens with sophisticated identity services at relatively low cost.
T he global digital identity market was valued at $42.12 billion in 2024 and is projected to grow to $133.19 billion by 2030, highlighting both the risks and opportunities inherent in the coming transformation (Research and Markets, 2024). Gartner research estimates that blockchain solutions could create $176 billion in business value by 2025, with identity applications representing a significant component. This value creation stems from reduced administrative costs, improved security, enhanced user experiences, and new business models enabled by user-controlled data.
The Netherlands conducted a comprehensive economic impact assessment of SSI implementation, concluding that national adoption could provide monetary benefits exceeding 1 billion euros through reduced administrative burden, improved service delivery, and enhanced security (van Ramshorst et al., 2021). These quantitative studies provide empirical support for policy investments in decentralized identity infrastructure and demonstrate the substantial economic opportunity from transitioning away from current centralized systems.
The economic implications extend beyond individual interactions to systemic market dynamics. Organizations conducting market research, governments seeking public input, and platforms trying to maintain community integrity all face the challenge of distinguishing authentic human participation from manufactured consensus. This has led to the emergence of what could be called “authentication markets,” where the ability to verify genuine human participation commands premium value, creating new economic opportunities for identity service providers.
SSI enables novel business models that were impossible under centralized identity architectures. Data cooperatives could emerge where users collectively monetize their information while retaining control. Identity service providers could compete on privacy, security, and user experience rather than data extraction capabilities.
The ability to port credentials across services creates opportunities for specialized identity service providers that focus on specific niches (such as professional credentials, educational achievements, and health records) while remaining interoperable with broader identity ecosystems. This specialization could drive innovation and improvements in efficiency.
D espite growing academic interest, empirical research on the economic impacts of decentralized identity systems remains limited. Longitudinal studies measuring productivity gains from reduced identity friction, quantitative analyses of network effects in identity platforms, and comparative studies of different technical approaches would strengthen the evidence base for policy decisions.
The complexity of identity systems requires interdisciplinary research approaches that combine computer science, economics, law, and behavioral psychology. Understanding how users interact with self-sovereign identity systems, what drives adoption decisions, and how different technical designs affect user behavior represents critical research priorities.
Regulatory frameworks for decentralized identity systems necessitate careful analysis to strike a balance between promoting innovation and protecting consumers. Research on regulatory sandboxes, cross-border identity recognition mechanisms, and privacy-preserving compliance frameworks would inform the development of effective policies.
The international dimensions of identity systems also require attention. As digital interactions increasingly cross national boundaries, questions of jurisdiction, mutual recognition, and regulatory arbitrage become economically significant. Research on international cooperation frameworks and diplomatic approaches to identity governance would support policy coordination.
T he evidence for recapturing control over personal data and identity through decentralized technologies is compelling from both economic and technological perspectives. Current centralized identity systems impose massive costs on the global economy while concentrating power among technology oligopolies and denying users fundamental control over their digital lives. The convergence of technological capabilities in blockchain and cryptography, combined with regulatory pressure from privacy laws, growing user awareness of data rights, and the urgent need to address AI-driven synthetic content, creates unprecedented opportunities for transformation.
The absence of an identity layer in the internet’s original architecture has created the conditions for surveillance capitalism and platform monopolies that extract value from users while imposing systemic risks. As AI becomes increasingly sophisticated and capable of generating convincing synthetic content, the “trust premium” for verified human interaction will only grow, making authentication markets increasingly valuable.
Self-sovereign identity systems offer a path toward user-controlled identity management that could reduce transaction costs, enhance privacy, and enable new forms of value creation. The First Person Project’s relationship-based verification approach represents an up-and-coming solution that strikes a balance between preserving privacy and verifying authenticity. Web3 frameworks provide the architectural foundation for distributed data storage and user-controlled digital vaults, addressing the issues associated with centralized management of personal data.
The transition to decentralized identity systems will not occur automatically. It requires coordinated action by governments, technology companies, standards bodies, and civil society organizations. Early adopters face coordination challenges and implementation costs, while the benefits of network effects accrue primarily after achieving critical mass adoption. However, innovative policy approaches, such as Switzerland’s SWIYU initiative and the EU’s Digital Identity Wallet framework, demonstrate regulatory pathways that support innovation while protecting user rights.
The economic case for action is clear. More fundamentally, the shift toward user-controlled identity systems could redistribute power in digital markets, enhance individual privacy and autonomy, and lay the groundwork for more equitable and sustainable digital economic growth. The question is not whether centralized identity systems will be replaced, but how quickly and effectively the transition can be managed to maximize economic benefits while minimizing disruption in an increasingly AI-dominated digital landscape. As artificial intelligence capabilities continue to advance, the arms race between synthetic content generation and detection will likely intensify. Proof-of-personhood systems may become essential infrastructure for maintaining authentic human discourse in digital spaces. The ongoing discussions exemplified by the Global Digital Collaboration conference in Geneva represent just the beginning of a broader transformation in how we think about identity, trust, and authenticity in digital spaces-one where individuals retain control over their identity while contributing to a more trustworthy and democratic digital ecosystem.
The evidence for recapturing control over personal data and identity through decentralized technologies is compelling from both economic and technological perspectives. Current centralized identity systems impose massive costs on the global economy while concentrating power among technology oligopolies and denying users fundamental control over their digital lives. The convergence of technological capabilities in blockchain and cryptography, combined with regulatory pressure from privacy laws and growing user awareness of data rights, creates unprecedented opportunities for transformation.
Self-sovereign identity systems offer a path toward user-controlled identity management that could reduce transaction costs, enhance privacy, and enable new forms of value creation. Proof-of-personhood protocols address fundamental challenges in ensuring a unique digital identity while preserving privacy and preventing surveillance. Together, these technologies provide foundations for a digital identity infrastructure that serves human agency rather than corporate extraction. The research demonstrates that the tools and techniques necessary for transformation already exist. What remains is the collective will to implement them in the service of human flourishing rather than corporate profit maximization. The transition to decentralized identity systems will not occur automatically. It requires coordinated action by governments, technology companies, standards bodies, and civil society organizations. Early adopters face coordination challenges and implementation costs, while the benefits of network effects accrue primarily after achieving critical mass adoption.
The Landscape Explorer is Currently Under Development
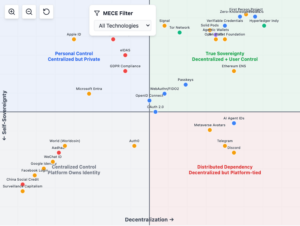
The Digital Identity Landscape Explorer is an interactive visualization mapping 70+ identity technologies across two critical dimensions: Decentralization and Self-Sovereignty. Based on a comprehensive MECE (Mutually Exclusive, Collectively Exhaustive) framework, it provides a structured analysis of how different identity solutions balance user control with technical architecture choices.
This landscape explorer serves as a strategic tool for understanding how identity technologies balance user empowerment with practical implementation constraints, helping stakeholders make informed decisions about digital identity architecture and policy.
The Identity Landscape Explorer illustrates that the complexity of an identity layer can only be addressed by drawing on multiple concepts and technologies. While a robust trust framework, in terms of binding commitments to the rules of the game, remains essential, the mechanisms of the blockchain can be leveraged to access personal data stores and handle value transfers, in particular. There will not be a single, centrally owned solution or architecture but rather a consortium of different, autonomous solution providers with their interoperable components.
MECE Framework Integration
The visualization incorporates all six layers of the digital identity MECE framework:
👥 Subject Types: What entities are being identified (humans, organizations, devices, AI agents)
🔐 Verification Mechanisms: How identity is proven (biometrics, cryptography, social proof)
🏗️ Data Architecture: How identity data is stored and managed
📜 Credentials & Assertions: What information is shared and trusted
⚖️ Governance & Trust: Who controls trust and sets the rules
🤝 Interaction Layer: How users and systems interact with identity
Key Insights
Technology Clustering Patterns
- Standards gravitate toward balance: Technical specifications tend toward medium decentralization with varying self-sovereignty
- Government systems cluster low: State-issued identities prioritize control over user agency
- Privacy tools span quadrants: Different approaches to protecting user privacy
- Enterprise solutions centralize: Business needs drive toward managed, centralized approaches
Emerging Trends
- SSI movement: Growing adoption of self-sovereign identity principles
- Privacy regulations: GDPR and similar laws pushing toward user control
- Web3 identity: Blockchain-based solutions exploring new paradigms
- Government digitization: National digital ID programs balancing convenience with control
Trade-offs and Tensions
- Usability vs. Control: More user control often means more complexity
- Privacy vs. Convenience: Strong privacy can reduce seamless experiences
- Decentralization vs. Performance: Distributed systems may have latency/reliability challenges
- Sovereignty vs. Interoperability: Highly sovereign solutions may have adoption barriers
Decentralization Percentage Drivers
The X-axis percentage is calculated based on these weighted factors:
Infrastructure Distribution (40% weight)
- 90-100%: Fully distributed networks (Bitcoin, IPFS, Hyperledger Indy)
- 70-90%: Blockchain/DLT-based with some centralization (Ethereum ENS, Ceramic)
- 50-70%: Federated systems with multiple providers (Matrix Protocol, SAML)
- 30-50%: Cloud services with regional distribution (Auth0, AWS Cognito)
- 0-30%: Single-provider centralized systems (Google, Facebook, WeChat)
Governance Structure (30% weight)
- High (80-100%): Community/DAO governance, open protocols
- Medium-High (60-80%): Multi-stakeholder governance, standards bodies
- Medium (40-60%): Enterprise federation, government frameworks
- Low (20-40%): Platform policies with user input
- Very Low (0-20%): Unilateral corporate or state control
Data Storage Architecture (20% weight)
- Fully Distributed: Data stored across multiple nodes/peers
- User-Controlled: Local storage or user-chosen providers
- Federated: Data distributed among trusted partners
- Cloud-Distributed: Multi-region but single-provider storage
- Centralized: Single database/data center control
Standards Openness (10% weight)
- Open Standards: W3C, IETF, ISO specifications
- Industry Standards: Consortium-developed protocols
- Proprietary with APIs: Closed but interoperable
- Platform-Specific: Limited interoperability
- Completely Closed: No external integration
Self-Sovereignty Percentage Drivers
The Y-axis percentage is calculated based on these weighted factors:
User Data Control (35% weight)
- 90-100%: Complete user ownership and portability (SSI wallets, KeePass)
- 70-90%: User-controlled with some service dependencies (Signal, 1Password)
- 50-70%: User choice with platform constraints (Apple ID, BankID)
- 30-50%: Limited user controls and export options (Microsoft Entra, Okta)
- 0-30%: Platform owns and controls all data (Google, Facebook, Aadhaar)
Privacy & Consent Granularity (25% weight)
- High (80-100%): Granular consent, minimal data collection, privacy-by-design
- Medium-High (60-80%): Good privacy controls, opt-in data sharing
- Medium (40-60%): Basic privacy settings, some user choice
- Low (20-40%): Limited privacy controls, opt-out mechanisms
- Very Low (0-20%): Minimal privacy, extensive tracking and profiling
Identity Portability (20% weight)
- Fully Portable: Standards-based, works across all systems
- Mostly Portable: Works across many systems with some friction
- Limited Portability: Platform-specific with some export options
- Vendor Lock-in: Difficult to migrate, proprietary formats
- No Portability: Completely siloed, no data export
Verification Independence (20% weight)
- Self-Verifiable: Cryptographic proofs, no third-party needed
- Peer-Verifiable: Community or network verification
- Multi-Party: Requires multiple authorities, but user choice
- Single Authority: Platform or government verification required
- Surveillance-Based: Continuous monitoring and control
Scoring Examples
High Decentralization + High Self-Sovereignty: W3C DIDs (85%, 92%)
Decentralization (85%):
- Infrastructure: 95% (Fully distributed, no central servers)
- Governance: 90% (W3C open standards, community-driven)
- Data Storage: 80% (User-controlled, multiple implementation options)
- Standards: 95% (Open W3C specification)
Self-Sovereignty (92%):
- User Control: 95% (Complete ownership of identifier and keys)
- Privacy: 90% (Privacy-by-design, selective disclosure)
- Portability: 95% (Works across all DID-compatible systems)
- Verification: 90% (Cryptographically self-verifiable)
Low Decentralization + Low Self-Sovereignty: Google Identity (15%, 25%)
Decentralization (15%):
- Infrastructure: 10% (Single company, multiple data centers)
- Governance: 5% (Unilateral Google control)
- Data Storage: 20% (Google’s distributed infrastructure)
- Standards: 25% (Some open protocols, but Google-controlled)
Self-Sovereignty (25%):
- User Control: 20% (Google owns account, limited export)
- Privacy: 15% (Extensive tracking, limited granular controls)
- Portability: 30% (Some data export, but platform-specific)
- Verification: 35% (User can verify account, but Google mediates)
Balanced Federation: OpenID Connect (50%, 55%)
Decentralization (50%):
- Infrastructure: 60% (Multiple identity providers possible)
- Governance: 70% (Open standard, multi-stakeholder)
- Data Storage: 40% (Varies by implementation)
- Standards: 90% (Open IETF/OpenID Foundation standard)
Self-Sovereignty (55%):
- User Control: 50% (Depends on IdP choice, some portability)
- Privacy: 60% (Consent flows, but varies by provider)
- Portability: 65% (Standard protocol enables switching)
- Verification: 45% (Requires trusted IdP, but user choice)
Two Dimensions
X-Axis: Decentralization (0-100%)
Definition: The degree to which identity data, verification processes, and governance are distributed across multiple nodes rather than controlled by a single entity.
Y-Axis: Self-Sovereignty (0-100%)
Definition: The extent to which individuals or entities have agency and control over their own identity data, credentials, and privacy decisions.
Four Identity Paradigms
The intersection of these dimensions creates four distinct quadrants:
True Sovereignty (High Decentralization + High Self-Sovereignty)
User-controlled identity with distributed infrastructure
Examples: W3C DIDs, Zero-Knowledge Proofs, Bitcoin Identity
Personal Control (Low Decentralization + High Self-Sovereignty)
Centralized systems prioritizing user privacy and control
Examples: Signal, Apple ID, KeePass
Distributed Dependency (High Decentralization + Low Self-Sovereignty)
Decentralized infrastructure with platform dependencies
Examples: Ethereum ENS, Telegram, AI Agent IDs
Centralized Control (Low Decentralization + Low Self-Sovereignty)
Traditional platforms control user identity and data
Examples: Google Identity, Facebook Login, Aadhaar
References Chapter 6:
Acquisti, A., Taylor, C., & Wagman, L. (2016). The economics of privacy. Journal of Economic Literature, 54(2), 442-492.
Adler, S., Hitzig, Z., Jain, S., Brewer, C., Chang, W., DiResta, R., Lazzarin, E., McGregor, S., Seltzer, W., Siddarth, D., Soliman, N., South, T., Spelliscy, C., Sporny, M., Srivastava, V., Bailey, J., Christian, B., Critch, A., Falcon, R., … Zick, T. (2025). Personhood credentials: Artificial intelligence and the value of privacy-preserving tools to distinguish who is real online. arXiv. https://doi.org/10.48550/arXiv.2408.07892
Akerlof, G. A., & Kranton, R. E. (2000). Economics and identity. Quarterly Journal of Economics, 115(3), 715-753.
Alaimo, C., & Kallinikos, J. (2017). Computing the Everyday: Social Media as Data Platforms. The Information Society, 33(4), 175-191. https://doi.org/10.1080/01972243.2017.1318327
Barabási, A. L., & Pósfai, M. (2016). Network science. Cambridge University Press.
Bargh, J. A., McKenna, K. Y. A., & Fitzsimons, G. M. (2002). Can you see the real me? Activation and expression of the “true self” on the Internet. Journal of Social Issues, 58(1), 33–48. https://doi.org/10.1111/1540-4560.00247
Bassi, E., Bandirali, M. (2023). The evolution of Web 3 and decentralized governance. Advances in web technologies and engineering book series, 108–129. http://dx.doi.org/10.4018/978-1-6684-9919-1.ch007
Belleflamme, P., & Peitz, M. (2018). Platforms and network effects. In Handbook of Game Theory and Industrial Organization (pp. 286-317). Edward Elgar Publishing. http://dx.doi.org/ 10.13140/ RG.2.2.35908.83848
Banerjee, A., Sevillano, J., & Higginson, M. (2024). From ripples to waves: The transformational power of tokenizing assets. McKinsey & Company. Retrieved July 10, 2025, from https://www.mckinsey.com/industries/financial-services/our-insights/from-ripples-to-waves-the-transformational-power-of-tokenizing-assets
Borge, M., Kokoris-Kogias, E., Jovanovic, P., Gasser, L., Gailly, N., & Ford, B. (2017). Proof-of-personhood: Redemocratizing permissionless cryptocurrencies. IEEE European Symposium on Security and Privacy Workshops, 23-26.
Buterin, V., (2023). What do I think about biometric proof of personhood? Retrieved July 10, 2025, from https://vitalik.eth.limo/general/2023/07/24/biometric.html
Cameron, K. (2005). The laws of Identity – Kim Cameron’s Identity Weblog. Retrieved July 3, 2025, from https://www.identityblog.com/?p=352
Cooper, M. (2025). Digital identities will empower consumers. UNCX. Retrieved July 10, 2025, https://uncx.substack.com/p/digital-identities-will-empower-consumers
Cuypers, I. R., Hennart, J. F., Silverman, B. S., & Ertug, G. (2021). Transaction cost theory: Past progress, current challenges, and suggestions for the future. Academy of Management Annals, 15(1), 111-150.
Dunphy, P., & Petitcolas, F. A. (2018). A first look at identity management schemes on the blockchain. IEEE Security & Privacy, 16(4), 20-29.
Eisenmann, T. R., Parker, G., & Van Alstyne, M. W. (2011). Platform envelopment. Strategic Management Journal, 32(12), 1270–1285.
Fairfield, J. a. T. (2017). owned. Cambridge University Press. https://doi.org/ 10.1017/ 9781316671467
Finck, M. (2019). Blockchain regulation and governance in Europe. Cambridge University Press.
Gartner. (2018). Blockchain-Based Transformation: A Gartner Trend Insight report (Report No. G00352362). Retrieved July 10, 2025, from https://emt.gartnerweb.com/ngw/globalassets/en/doc/documents/3869696-blockchain-based-transformation-a-gartner-trend-insight-report.pdf
Granic, A., Loboda, A., & Dzigurski, M. (2021). Digital trust and its impact on economic performance. Information Technology for Development, 27(3), 401-418.
Grech, A., Sood, I., & Ariño, L. (2021). Blockchain, self-sovereign identity and digital credentials: Promise versus praxis in education. Frontiers in Blockchain, 4, 616779.
Hayat, Z. (2022). Digital trust: How to unleash the trillion-dollar opportunity for our global economy. World Economic Forum. Retrieved July 8, 2025, from https://www.weforum.org/stories/2022/08/digital-trust-how-to-unleash-the-trillion-dollar-opportunity-for-our-global-economy/
Jones, C. R., & Bergen, B. K. (2024). People cannot distinguish GPT-4 from a human in a Turing test (No. arXiv:2405.08007). arXiv. https://doi.org/10.48550/arXiv.2405.08007
Kondova, G., & Erbguth, J. (2020). Self-sovereign identity on public blockchains and the GDPR. Proceedings of the 35th Annual ACM Symposium on Applied Computing, 342-345.
Milgram, S. (1967). The small-world problem. Psychology Today, 1(1), 61-67.
Mühle, A., Grüner, A., Gayvoronskaya, T., & Meinel, C. (2018). A survey on essential components of a self-sovereign identity. Computer Science Review, 30, 80-86. https://doi.org/10.1016/ j.cosrev.2018.10.002
Nguyen, C. M.-H., Haynes, P., Maguire, S., & Friedberg, J. (2013). A user-centred approach to the data dilemma: Context, architecture, and policy. In M. Hildebrandt et al. (Eds.), Digital Enlightenment Yearbook 2013 (pp. 227-242). IOS Press. https://doi.org/10.3233/978-1-61499-295-0-227
Preukschat, A., & Reed, D. (2021). Self-sovereign identity: Decentralized digital identity and verifiable credentials. Manning Publications.
Reed, D., & O’Donnell, D. (2025). Introduction to Ayra and the First Person Project. Proceedings of the 40th Annual Internet Identity Workshop. Retrieved July 10, 2025, from of-proceedings-xl-spring-2025.pdf
Research and Markets (2024). Digital Identity Solutions Mardket Trends and Shares, Forecast to 2030: Government regulations and ID Wallet solutions propdl industry growth. GlobeNewswire News Room. Retrieved July 2, 2025, from https://www.globenewswire.com/news-release/2024/12/13/2996725/28124/en/Digital-Identity-Solutions-Market-Trends-and-Shares-Forecast-to-2030-Government-Regulations-and-ID-Wallet-Solutions-Propel-Industry-Growth.html
Robb, C. A., & Wendel, S. (2022). Who can you trust? Assessing vulnerability to digital imposter scams. Journal of Consumer Policy, 46(1), 27-51. https://doi.org/10.1007/s10603-022-09531-6
Rost, K., Stahel, L., & Frey, B. S. (2016). Digital social norm enforcement: Online firestorms in social media. PLOS ONE, 11(6), e0155923. https://doi.org/10.1371/journal.pone.0155923
Searls, D. (2014). Why we need first person technologies on the Net – ProjectVRM. Retrieved July 5, 2025, from https://projectvrm.org/2014/03/19/why-we-need-first-person-technologies-on-the-net/
Shapiro, C., & Varian, H. R. (1999). Information rules: A strategic guide to the network economy. Harvard Business Press.
Smith, J. (2025). Yes, but when will the digital ID market take off? Customer Futures. Retrieved July 10, 2025, from https://www.customerfutures.com/p/the-usp-for-the-eu-digital-identity
Srnicek, N. (2017). Platform capitalism. Polity Press.
Stockburger, L., Kokosioulis, G., Mukkamala, A., Mukkamala, R., & Avital, M. (2021). Decentralized identity management: A survey on architecture, applications, and challenges. IEEE Access, 9, 80154-80175.
van Ramshorst, C., Kluiters, L., van der Harst, E., Jansen, V., den Breeijen, S., & van Deventer, O. (2021). SSI speelveldanalyse: Een verkenning van het Nederlandse SSI speelveld, toekomstige ontwikkelrichtingen, impact op publieke waarden en de rol van de Nederlandse overheid. TNO & INNOPAY. Retrieved July 11, 2025, from https://www.eerstekamer.nl/overig/ 20211029/eindrapport_nederlandse/document
Wang, F., & De Filippi, P. (2020). Self-sovereign identity in a globalized world: Credentials-based identity systems as a driver for economic inclusion. Frontiers in Blockchain, 2, 28. https://doi.org/10.3389/fbloc.2019.00028
Windley, P. (n.d.). Establishing first person digital trust. Retrieved July 10, 2025, from dddsdhttps://windley.com/archives/2025/04/establishing_first_person_digital_trust.shtml
World Economic Forum. (2013). Unlocking the value of personal data: From collection to usage. World Economic Forum. Retrieved July 4, 2025, from https://www.weforum.org/reports/unlocking-the-value-of-personal-data-from-collection-to-usage
Yang, R., Yu, F. R., Si, P., Yang, Z., & Zhang, Y. (2019). Integrated blockchain and edge computing systems: A survey, some research issues and challenges. IEEE Communications Surveys & Tutorials, 21(2), 1508-1532. http://dx.doi.org/10.1109/COMST.2019.2894727
Zheng, Z., Xie, S., Dai, H., Chen, X., & Wang, H. (2018). Blockchain challenges and opportunities: A survey. International Journal of Web and Grid Services, 14(4), 352-375. http://dx.doi.org/ 10.1504/IJWGS.2018.095647
Zholudev, V., Kalaydin, P. G., Novoselsky, A., & Petrov, T. (2023). SuMSub expert roundtable: The top KYC trends coming in 2024. Sumsub. Retrieved July 10, 2025, from https://sumsub.com/ blog/top-kyc-trends
Zuboff, S. (2019). The age of surveillance capitalism: The fight for a human future at the new frontier of power. PublicAffairs.